




With the increasing sophistication of cyber threats, businesses face mounting pressure to safeguard their digital assets. Managed Vulnerability Assessment (VA) and Penetration Testing (Pen Testing) are two vital strategies that help identify and address security weaknesses before they can be exploited. While Managed VA focuses on systematically detecting vulnerabilities through continuous monitoring, Pen Testing simulates real-world attacks to uncover exploitable gaps in defences.
The importance of these practices cannot be overstated—cyberattacks have surged globally, with studies showing a 38% rise in attacks on Australian organisations in 2024 alone. The financial and reputational consequences of these breaches underscore the need for proactive security measures.
This article provides a clear comparison of Managed VA and Pen Testing, outlining their unique roles in cybersecurity. By understanding these differences, businesses can make informed decisions about which approach aligns best with their cybersecurity needs.
A Managed Vulnerability Assessment (VA) is a proactive security measure designed to identify, evaluate, and prioritise vulnerabilities in an organisation’s systems, applications, and networks. Unlike ad hoc assessments, Managed VA is an ongoing process that provides organisations with regular insights into their security posture, enabling them to address risks promptly. Its primary goal is to ensure vulnerabilities are detected and mitigated before they can be exploited.
The methodology of Managed VA involves three key stages:
The benefits of Managed VA include continuous monitoring that allows organisations to maintain a real-time view of their vulnerabilities and cost-effectiveness, as automated processes reduce the need for extensive manual intervention. According to the Australian Cyber Security Centre’s (ACSC) Vulnerability Management Guidelines, regular vulnerability assessments are crucial for protecting against attacks, especially in industries like healthcare and finance, where sensitive data is targeted.
For example, a 2024 ACSC report revealed that Australian businesses experienced a 60% reduction in successful breaches when using Managed VA in conjunction with other security measures. This underscores the effectiveness of this approach in reducing risk and improving resilience.
Penetration Testing, often referred to as Pen Testing, is a controlled and systematic process that simulates real-world cyberattacks to assess the security of an organisation’s systems, networks, and applications. Unlike vulnerability scanning, which identifies known weaknesses using automated tools, Pen Testing goes deeper by actively exploiting vulnerabilities to determine the extent of potential damage if those weaknesses were exploited by malicious actors.
The methodology behind Pen Testing involves several steps:
The benefits of Pen Testing are substantial. It goes beyond surface-level assessments to uncover complex security gaps, such as misconfigurations or zero-day vulnerabilities, that could otherwise remain undetected. Pen Testing also strengthens an organisation’s incident response readiness, providing actionable insights into how defences perform under attack.
Australian cybersecurity standards, including ISO 27001, emphasise the importance of Pen Testing in maintaining compliance. These standards recommend periodic testing to validate the effectiveness of security controls and demonstrate an organisation’s commitment to proactive risk management. According to the Australian Cyber Security Centre (ACSC), organisations that adopt Pen Testing as part of their strategy are better positioned to prevent breaches and maintain operational resilience.
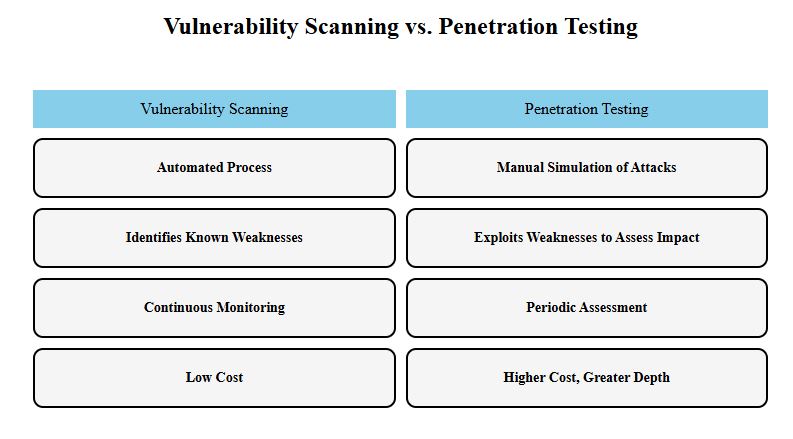
Understanding the distinctions between Managed Vulnerability Assessment (VA) and Penetration Testing (Pen Testing) is crucial for developing a robust cybersecurity strategy. Both approaches address vulnerabilities but differ significantly in methodology, objectives, frequency, and resource requirements. Below is a detailed comparison.
Managed VA relies on automated tools to identify and prioritise vulnerabilities across systems. It provides a continuous assessment of an organisation’s security posture, offering insights into areas requiring remediation. Conversely, Pen Testing involves manual simulation of real-world attacks by ethical hackers to exploit vulnerabilities and assess their potential impact.
The goal of Managed VA is to ensure consistent vulnerability detection and mitigation. It is a preventive measure focused on reducing the attack surface. Pen Testing, on the other hand, seeks to test an organisation’s defences under attack conditions, helping improve incident response and uncover complex vulnerabilities.
Managed VA is an ongoing process, ideal for maintaining real-time awareness of vulnerabilities. Pen Testing is conducted periodically, often as part of compliance requirements or after significant infrastructure changes.
Managed VA is generally more cost-effective due to automation, requiring fewer resources to operate. Pen Testing, being resource-intensive and dependent on skilled professionals, is comparatively expensive but provides in-depth insights.
According to the Australian Cyber Security Centre (ACSC), combining these approaches results in a 65% improvement in threat mitigation effectiveness for Australian businesses. Source: ACSC.
| Aspect | Managed Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Methodology | Automated scanning and prioritisation | Manual simulation of real-world attacks |
| Goals | Prevent vulnerabilities from being exploited | Test defences and uncover exploitable gaps |
| Frequency | Continuous | Periodic |
| Costs | Lower due to automation | Higher due to manual effort |
| Outcomes | Ongoing vulnerability management | Improved incident response readiness |
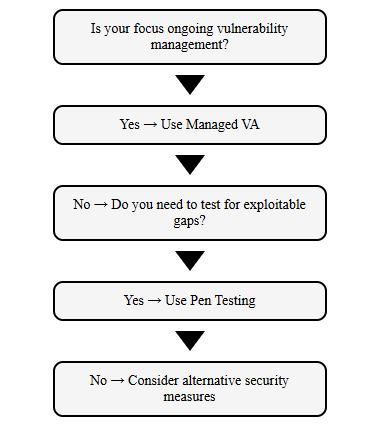
Choosing between Managed Vulnerability Assessment (VA) and Penetration Testing (Pen Testing) depends on the organisation’s cybersecurity objectives, resources, and regulatory requirements. Each method has distinct use cases and benefits.

While Managed Vulnerability Assessment (VA) and Penetration Testing (Pen Testing) serve distinct purposes, their integration provides a layered cybersecurity strategy essential for defending against evolving threats. Combining these approaches ensures both the identification of vulnerabilities and the assessment of their exploitability, offering a holistic security framework.
Managed VA delivers continuous monitoring and prioritisation of vulnerabilities, ensuring that security gaps are regularly identified and addressed. However, it may not detect sophisticated attack vectors or provide insights into the actual impact of a breach. Pen Testing complements this by simulating real-world attack scenarios, uncovering complex security gaps that may not be apparent through automated scans.
The NIST Cybersecurity Framework recommends a layered approach to security, integrating continuous vulnerability assessments with advanced testing methodologies to create a resilient system. For instance, an Australian financial institution might use Managed VA to monitor their systems daily while scheduling Pen Testing quarterly to simulate attacks on high-value assets, such as payment gateways. This dual approach enables the organisation to proactively manage risks while validating their defences under attack conditions.
By leveraging both tools, businesses enhance their security posture, meeting compliance requirements and building resilience against increasingly sophisticated cyber threats. Layered cybersecurity ensures organisations can mitigate risks effectively, protect critical data, and maintain operational integrity.
Selecting between Managed Vulnerability Assessment (VA) and Penetration Testing requires careful consideration of your organisation’s size, available resources, and cybersecurity goals. While Managed VA provides ongoing visibility into vulnerabilities, Pen Testing offers deeper insights into potential exploitability. Together, they form a robust, layered defence strategy that strengthens an organisation’s security posture.
For smaller businesses, Managed VA is often a cost-effective starting point, enabling continuous vulnerability management. Larger enterprises or those in highly regulated industries may require periodic Pen Testing to ensure compliance and safeguard high-value assets. Understanding these differences allows businesses to make informed decisions that align with their specific needs.
At Fort1, we specialise in tailored cybersecurity solutions, combining Managed VA and Pen Testing Services to help businesses achieve comprehensive protection. Contact us today to discuss how we can enhance your organisation’s defences and ensure compliance with Australian cybersecurity standards. Visit Fort1’s Cybersecurity Solutions to learn more or request a consultation.
Make cybersecurity a priority with Fort1—your trusted partner in safeguarding your digital assets.

Fort1 provides comprehensive cybersecurity solutions tailored to protect your business from evolving digital threats. With expertise in penetration testing, dark web monitoring, and managed detection services, we empower organisations to stay secure and resilient in the face of modern cyber challenges.
Copyright @2024 Fort1. All Rights Reserved by Fort1.