




Managed Vulnerability Assessment (MVA) and Penetration Testing (PT) are two essential cybersecurity measures that work together to protect organisations from cyber threats. Cyber threats are evolving at an unprecedented rate, with organisations facing an increasing number of sophisticated attacks each year. According to the Australian Cyber Security Centre (ACSC), there were over 76,000 cybercrime reports in the 2022-23 financial year, a 23% increase from the previous year. This growing threat landscape underscores the need for a multi-layered cybersecurity strategy that combines both proactive and reactive defence mechanisms.
Two fundamental components of this strategy are Managed Vulnerability Assessment (MVA) and Penetration Testing (PT). MVA is a continuous and automated process that identifies security vulnerabilities across an organisation’s digital infrastructure, allowing businesses to address potential weaknesses before they can be exploited. In contrast, Penetration Testing (PT) involves ethical hacking simulations to assess how real-world attackers might exploit these vulnerabilities. While MVA focuses on detection and risk assessment, PT goes further by validating exploitability and assessing real-world impact.
Despite their differences, neither MVA nor PT alone is sufficient to ensure cybersecurity resilience. A vulnerability scan may detect thousands of issues, but without penetration testing, organisations may struggle to determine which pose the most immediate risk. Likewise, conducting penetration tests without ongoing vulnerability assessments may leave significant security gaps between testing cycles.
This article explores how Managed Vulnerability Assessment and Penetration Testing complement each other to form a robust cybersecurity defence system. By integrating these complementary approaches, organisations can enhance their risk mitigation strategies, improve compliance with frameworks like the ACSC Essential Eight, and strengthen their overall security posture.
Managed Vulnerability Assessment (MVA) is a continuous and automated process designed to identify and assess security vulnerabilities across an organisation’s digital environment. Unlike one-time security evaluations, MVA operates persistently, ensuring that newly emerging vulnerabilities are detected and prioritised based on risk severity.
MVA follows a structured approach to proactive cybersecurity management, consisting of four key stages:
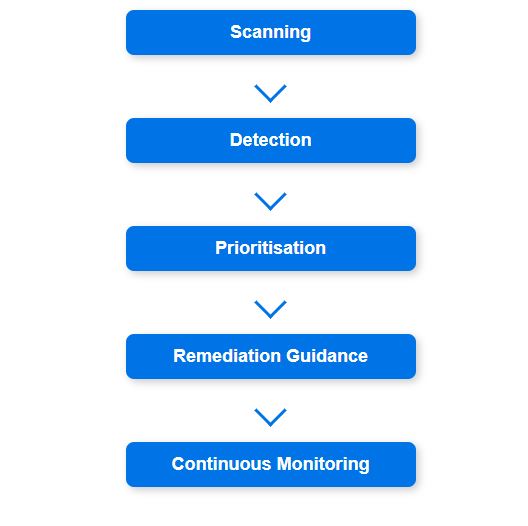
By incorporating Managed Vulnerability Assessment, organisations can maintain ongoing security visibility, improve risk prioritisation, and ensure compliance with cybersecurity regulations. However, MVA alone is insufficient, as it does not validate exploitability—which is where penetration testing plays a critical role.

Penetration Testing (PT) is a controlled cybersecurity exercise designed to simulate real-world cyberattacks and evaluate an organisation’s ability to detect and respond to security threats. Unlike automated vulnerability assessments, PT involves manual exploitation of security weaknesses by ethical hackers, commonly referred to as penetration testers.
PT is essential for assessing real-world attack resilience, as it simulates how cybercriminals exploit security gaps. By actively testing security defences, penetration testing helps organisations:
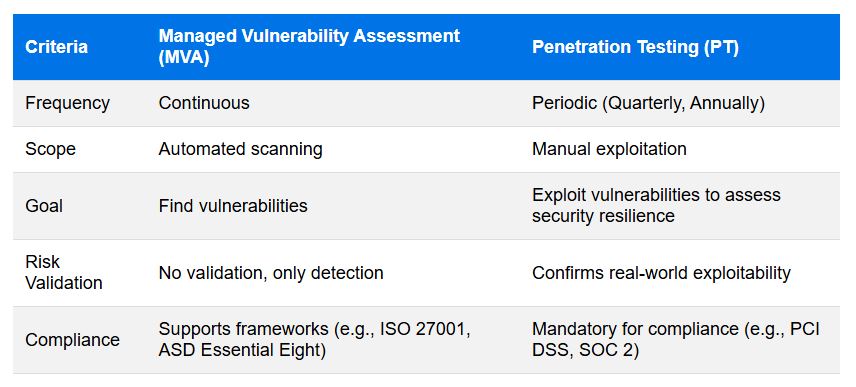
Penetration testing is a critical component of a robust cybersecurity strategy, ensuring that vulnerabilities identified through MVA are properly validated and mitigated. However, because PT is conducted periodically, it must be combined with continuous monitoring to provide comprehensive security coverage.
Penetration testing is a critical component of a robust cybersecurity strategy, ensuring that vulnerabilities identified through MVA are properly validated and mitigated. However, because PT is conducted periodically, it must be combined with continuous monitoring to provide comprehensive security coverage.
A combined approach integrating MVA for continuous detection and PT for real-world validation ensures a stronger cybersecurity posture.
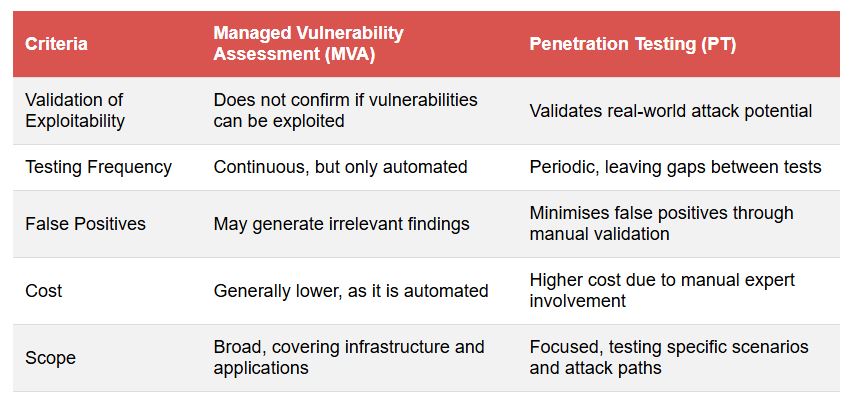
By integrating both MVA and PT, organisations can achieve continuous risk identification and in-depth attack validation, ensuring a comprehensive cybersecurity strategy.
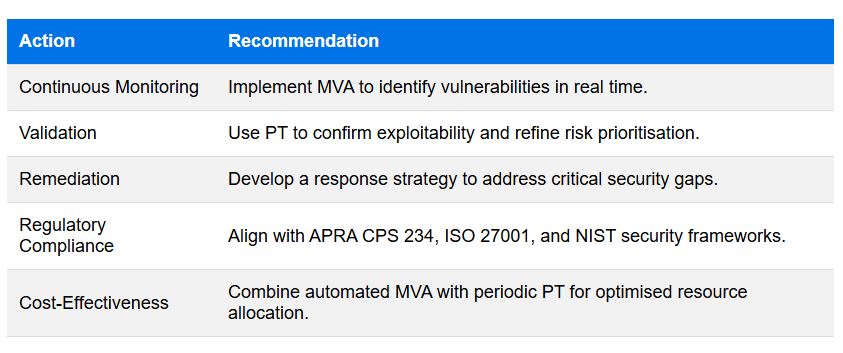
Managed Vulnerability Assessment (MVA) and Penetration Testing (PT) complement each other by providing both continuous vulnerability identification and real-world exploitability validation. While MVA ensures that security weaknesses are detected in real time, PT confirms whether these vulnerabilities pose a genuine risk. By integrating both approaches, organisations prioritise critical threats, reduce false positives, and optimise security investments.
The combined workflow of MVA and PT follows a structured approach:
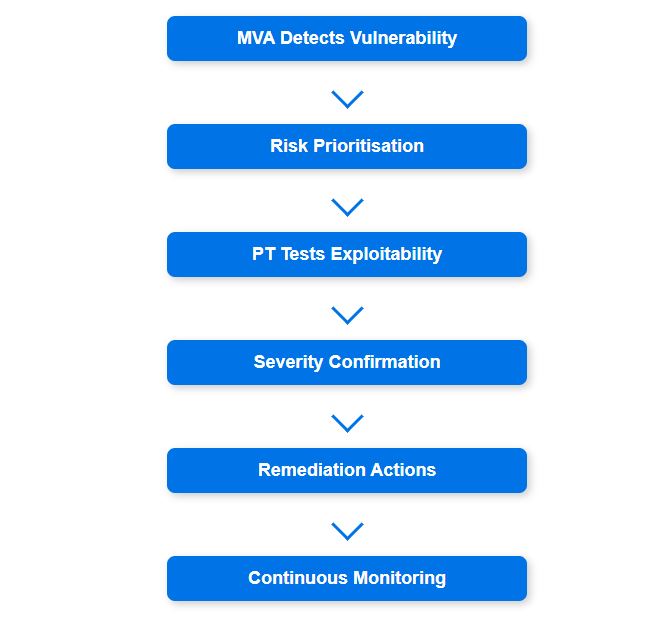
By combining automated MVA with targeted PT, organisations can detect vulnerabilities, validate risks, and implement remediation efforts efficiently, leading to a more resilient cybersecurity posture.

Many organisations across different industries rely on Managed Vulnerability Assessment (MVA) and Penetration Testing (PT) to strengthen their cybersecurity posture. The following case studies illustrate how the integration of these practices helps organisations meet compliance requirements, prevent data breaches, and secure critical infrastructure.
A major Australian financial institution adopted MVA and PT to comply with APRA CPS 234, which mandates that financial organisations must proactively manage security vulnerabilities. By implementing continuous vulnerability assessment, the bank detected unpatched software weaknesses in its online banking platform. Through targeted penetration testing, ethical hackers demonstrated how these vulnerabilities could lead to unauthorised access to customer accounts. The findings enabled the security team to remediate high-risk issues, ensuring regulatory compliance and preventing potential fraud.
A rapidly growing e-commerce company faced repeated cyberattack attempts, including credential stuffing and SQL injection attacks. While MVA continuously flagged vulnerabilities in the platform, it was penetration testing that confirmed attackers could exploit a misconfigured API endpoint. This validation prompted an immediate security fix, preventing customer data exposure and reinforcing consumer trust.
An Australian government agency responsible for public sector data storage integrated MVA and PT to safeguard its cloud environment from nation-state cyber threats. Regular MVA scans helped detect outdated encryption protocols, while penetration testing simulated targeted attacks on the system. As a result, the agency strengthened its zero-trust architecture, reducing the risk of data leaks and service disruptions.

By integrating MVA and PT, organisations across finance, e-commerce, government, and healthcare can strengthen cybersecurity resilience, prevent costly data breaches, and comply with regulatory standards.

Despite the benefits of Managed Vulnerability Assessment (MVA) and Penetration Testing (PT), many organisations encounter operational and financial obstacles when integrating these security practices.
By addressing these challenges through strategic security investments, organisations can optimise their cybersecurity defences while ensuring cost-effective risk mitigation.
Managed Vulnerability Assessment (MVA) and Penetration Testing (PT) are complementary cybersecurity practices that, when integrated, provide a comprehensive approach to risk management. While MVA ensures continuous security monitoring and early threat detection, PT validates exploitability and strengthens defensive strategies.
To maximise cybersecurity resilience, organisations should implement:
Organisations should ensure that their security practices align with Australian cybersecurity compliance standards, such as:
Cybersecurity threats continue to evolve, requiring businesses to adopt a multi-layered defence strategy. Managed Vulnerability Assessment (MVA) and Penetration Testing (PT) are essential components of this strategy, ensuring that organisations can identify, prioritise, and remediate security weaknesses effectively. While MVA provides continuous visibility into vulnerabilities, PT confirms which security gaps pose an immediate risk. Without a comprehensive approach, businesses remain vulnerable to undetected threats and unverified security flaws.
A proactive security strategy is critical for minimising risks, maintaining regulatory compliance, and strengthening cyber resilience. By combining automated MVA with scheduled PT, businesses can achieve better risk prioritisation, reduce false positives, and allocate resources efficiently.
At Fort1, we specialise in delivering comprehensive cybersecurity solutions tailored to organisations across various industries. Our MVA and PT services help businesses achieve continuous security monitoring and real-world threat validation, ensuring a robust cybersecurity posture.
Is your business prepared for the next cyber threat? Evaluate your security readiness today with Fort1’s expert cybersecurity services. Contact us at Fort1 to implement a proactive and resilient cybersecurity strategy.

Fort1 provides comprehensive cybersecurity solutions tailored to protect your business from evolving digital threats. With expertise in penetration testing, dark web monitoring, and managed detection services, we empower organisations to stay secure and resilient in the face of modern cyber challenges.
Copyright @2024 Fort1. All Rights Reserved by Fort1.