




As organisations increasingly migrate their operations to the cloud, securing sensitive data in these shared environments has become a critical priority. Recent statistics highlight the urgency: according to a 2023 report by Cybersecurity Ventures, global cybercrime costs are expected to reach $8 trillion annually, with a significant portion attributed to vulnerabilities in cloud environments.
Cloud penetration testing plays a pivotal role in identifying and mitigating these vulnerabilities before they can be exploited. Unlike traditional IT infrastructure, cloud environments are highly dynamic and rely on shared responsibility models where security obligations are split between the provider and the customer. This complexity often leads to misconfigurations, insecure application programming interfaces (APIs), and overly permissive access controls—each representing a significant risk.
For example, a misconfigured Amazon S3 bucket in 2022 exposed sensitive data from a global healthcare provider, affecting millions of patients worldwide. Such incidents underscore the importance of proactive measures like cloud penetration testing to prevent data breaches and maintain compliance with regulatory standards.
By identifying weaknesses in configurations, access controls, and APIs, cloud penetration testing empowers businesses to strengthen their security posture, ensuring the confidentiality, integrity, and availability of their cloud-hosted data. This essential practice is no longer optional but a necessary component of robust cloud security strategies.
The shift to cloud computing has revolutionised data storage and management, but it has also introduced unique vulnerabilities that demand proactive security measures. Cloud environments differ significantly from traditional infrastructures, with their dynamic nature, multi-tenant setups, and shared responsibility models creating a complex security landscape. Cloud penetration testing is essential for uncovering and addressing these challenges.
One of the most common risks in cloud environments is misconfigured storage buckets. In a well-documented case from 2022, a misconfigured AWS S3 bucket exposed sensitive data of 3 million users from a prominent e-commerce platform, highlighting the devastating impact of human error. These vulnerabilities have the potential to result in significant data breaches, substantial regulatory penalties, and harm to an organisation’s reputation.
Finally, weak authentication mechanisms, such as the lack of multi-factor authentication, remain a significant threat. In cloud environments, compromised credentials can result in unauthorised access to sensitive data or critical operations, further emphasising the need for robust security testing.
By identifying these risks, cloud penetration testing helps organisations secure their cloud infrastructure, maintain compliance with regulations like the Australian Privacy Act, and avoid costly breaches.
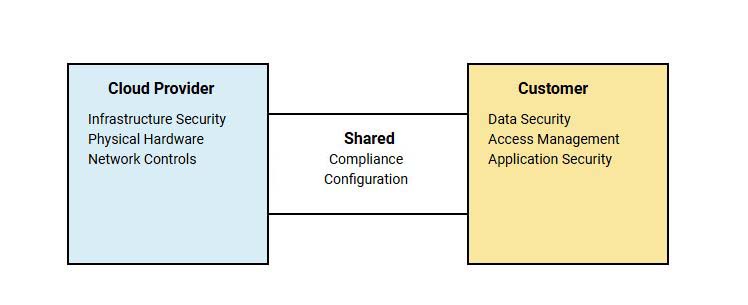
Cloud environments offer businesses unparalleled flexibility, but they also present unique vulnerabilities that, if left unaddressed, can lead to significant security incidents. Understanding these vulnerabilities is a critical step toward securing cloud infrastructure.
Misconfigurations remain the most common vulnerability in cloud environments. Examples include public-facing storage buckets or overly permissive access policies. A case in point is the 2019 incident where a publicly exposed AWS S3 bucket leaked over 1 billion records of sensitive financial data, impacting thousands of individuals and organisations. Misconfigurations often stem from human error or a lack of adherence to best practices.
Application programming interfaces (APIs) play a vital role in cloud environments by enabling integrations and data exchange. However, insecure APIs, such as those lacking proper authentication or encryption, pose a significant risk. For instance, a 2022 attack on a cloud service provider exploited an exposed API endpoint, granting attackers unauthorised access to sensitive customer data. The OWASP API Security Top 10 identifies such vulnerabilities, emphasising the importance of secure API development practices (source).
IAM weaknesses, such as overprovisioned permissions or poor password policies, create avenues for attackers to exploit user accounts. An overprivileged user account, for example, may inadvertently grant access to critical systems. Adopting principles like least privilege and implementing multi-factor authentication are essential strategies to mitigate these risks. The Australian Cyber Security Centre’s Cloud Security Guidelines provide a comprehensive framework for IAM best practices in cloud environments (source).
| Vulnerability | Description | Potential Impact |
|---|---|---|
| Misconfigurations | Public-facing storage, overly permissive access policies. | Data breaches, financial loss, reputational damage. |
| Insecure APIs | APIs lacking proper authentication or encryption. | Unauthorised access, data exfiltration. |
| IAM Weaknesses | Overprovisioned permissions, weak password policies. | Compromised accounts, insider threats. |
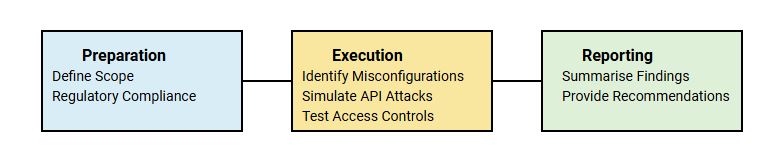
Cloud penetration testing involves a systematic approach designed to uncover vulnerabilities within cloud environments. By simulating real-world attack scenarios, it enables organisations to identify weaknesses and improve their security posture. The process can be divided into three primary stages: preparation, execution, and reporting.
The success of cloud penetration testing hinges on thorough preparation. The first step is to define the scope of the test, including whether the focus is on Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), or Software-as-a-Service (SaaS). Each model has unique risks and security considerations.
Legal and regulatory compliance is another critical aspect. Organisations must ensure that testing activities align with laws and regulations such as the Australian Privacy Act or contractual obligations with cloud service providers. Permission must be obtained before testing begins to avoid violating terms of service agreements.
The execution phase is where vulnerabilities are actively identified and assessed. This includes:
The final stage involves consolidating findings and providing actionable insights. A detailed report is prepared, summarising the vulnerabilities identified, their severity, and the potential impact on the organisation. The report also includes tailored recommendations for mitigating risks, improving compliance, and strengthening overall cloud security.
For instance, the NIST Cloud Security Recommendations provide a robust framework for assessing cloud environments and implementing best practices (source).
Cloud penetration testing offers businesses a proactive approach to safeguarding their digital assets in increasingly complex cloud environments. By identifying and addressing vulnerabilities before they can be exploited, this practice provides several tangible benefits.
One of the most significant advantages of cloud penetration testing is the enhancement of an organisation’s overall security posture. By uncovering misconfigurations, insecure APIs, and other weaknesses, businesses can implement targeted solutions to close security gaps. This reduces the likelihood of data breaches and ensures the confidentiality, integrity, and availability of sensitive information.
Regulatory frameworks such as ISO 27001 and the Australian Privacy Act mandate stringent data protection measures. Cloud penetration testing enables organisations to meet these compliance requirements by demonstrating their commitment to maintaining a secure cloud infrastructure. Regular testing also helps businesses prepare for audits and avoid penalties associated with non-compliance.
Cloud environments are frequent targets of sophisticated cyberattacks, including advanced persistent threats (APTs). Penetration testing simulates real-world attack scenarios, providing organisations with valuable insights into how their defences hold up against evolving threats. This process not only identifies vulnerabilities but also improves incident response readiness by exposing potential weaknesses in existing security protocols.
By integrating cloud security testing into their cybersecurity strategy, organisations can ensure their infrastructure remains robust, compliant, and resilient against advanced threats. Cloud penetration testing is not merely a technical exercise but a strategic necessity for securing cloud infrastructure effectively.

Cloud penetration testing, while indispensable, is not without its challenges. Recognising these obstacles and adopting best practices can ensure an effective and meaningful security testing process.
One of the primary challenges is the rapidly evolving nature of cloud environments. Cloud infrastructures are dynamic, with frequent updates, scaling, and reconfigurations, which can lead to new vulnerabilities that are difficult to track without continuous monitoring. This makes maintaining a consistent security posture a demanding task.
Another significant challenge lies in ensuring vendor collaboration. Cloud service providers often enforce strict terms of service that dictate how penetration testing can be conducted. Businesses must obtain explicit permissions to avoid breaching contractual agreements, which can complicate the testing process.
To address these challenges, regular testing and monitoring should be prioritised. Frequent assessments ensure that vulnerabilities introduced through changes to cloud environments are promptly identified and mitigated. Businesses should also implement continuous monitoring solutions to supplement penetration testing and provide real-time insights.
Additionally, findings from penetration tests must be incorporated into the broader security strategy. This involves addressing identified vulnerabilities, updating policies and configurations, and training staff on secure practices. These actions enhance the organisation’s ability to secure its cloud infrastructure against evolving threats.
By addressing these challenges and adhering to best practices, organisations can effectively secure their cloud environments and maintain resilience in an ever-changing digital landscape.
Cloud penetration testing is an essential practice for businesses seeking to protect their assets in an increasingly digital and interconnected environment. The complexity of cloud infrastructure, combined with its rapid adoption, has introduced unique security challenges that require proactive and specialised solutions. By identifying vulnerabilities such as misconfigurations, insecure APIs, and weak access controls, cloud penetration testing strengthens your organisation’s defences and ensures compliance with critical regulations like the Australian Privacy Act and ISO 27001.
Prioritising cloud security testing is not just a matter of compliance but a strategic necessity for maintaining trust and safeguarding sensitive data. To fortify your cloud environment and mitigate emerging threats, consult the experts at Fort1. Our tailored penetration testing services provide actionable insights to help you achieve a secure and resilient infrastructure.
Visit Fort1’s Cloud Security Services today to secure your cloud infrastructure and gain peace of mind in an evolving threat landscape.

Fort1 provides comprehensive cybersecurity solutions tailored to protect your business from evolving digital threats. With expertise in penetration testing, dark web monitoring, and managed detection services, we empower organisations to stay secure and resilient in the face of modern cyber challenges.
Copyright @2024 Fort1. All Rights Reserved by Fort1.