




The increasing adoption of blockchain technology across industries has introduced new security challenges distinct from those in traditional cybersecurity. Blockchain vs. traditional cybersecurity penetration testing is a crucial topic as Web3 ecosystems, including decentralised finance (DeFi), smart contracts, and NFTs, continue to expand. With rising threats, penetration testing plays a vital role in identifying vulnerabilities before attackers exploit them.
According to a report by Chainalysis (2023), blockchain-related cybercrime resulted in losses exceeding $3.8 billion in 2022, with DeFi platforms accounting for over 80% of the attacks. This highlights the urgency of robust penetration testing tailored for blockchain environments.
Traditional cybersecurity focuses on centralised network protection, addressing threats such as malware, phishing, and data breaches. In contrast, blockchain security revolves around decentralised architectures, where vulnerabilities often stem from faulty smart contracts, cryptographic flaws, and consensus mechanism exploits. Given these differences, penetration testing methodologies for Web3 security require a distinct approach compared to traditional IT infrastructure testing.
As digital threats evolve, cybersecurity strategies must adapt. Blockchain vs. traditional cybersecurity penetration testing plays a crucial role in securing digital infrastructures. While both aim to identify vulnerabilities before attackers exploit them, their methodologies differ significantly.
Traditional cybersecurity relies on centralized security models, protecting corporate networks and cloud environments with firewalls, intrusion detection systems, and endpoint protection. In contrast, blockchain security is built on decentralized principles, where vulnerabilities often arise from smart contracts, private key management, and governance models.
Given these differences, penetration testers need to approach Web3 security assessments differently than traditional IT audits. Understanding these distinctions is critical for businesses, developers, and security professionals working in both centralized and decentralized ecosystems.
Traditional cybersecurity is the practice of securing centralised digital systems such as corporate networks, databases, and cloud environments from cyber threats. Unlike Web3 cybersecurity challenges, which focus on decentralised architectures, traditional security relies on firewalls, intrusion detection systems (IDS), and endpoint protection to prevent unauthorised access, data breaches, and malware infections.
As cybercriminals continue to develop advanced attack techniques, organisations must implement robust penetration testing to identify vulnerabilities before they are exploited. The Australian Cyber Security Centre (ACSC) provides guidelines on best security practices for Australian businesses, reinforcing the importance of proactive threat assessments (ACSC, 2024).
Traditional IT infrastructures are vulnerable to a range of cyber threats, including:
Penetration testing in traditional cybersecurity aims to simulate real-world attacks on an organisation’s IT infrastructure. This approach helps businesses identify weaknesses before threat actors exploit them.
✅ Network Security Testing → Evaluates firewall configurations, network traffic, and access controls.
✅ Web Application Testing → Identifies vulnerabilities in websites and online services (e.g., OWASP Top 10 threats).
✅ Firewall & IDS Testing → Assesses how well intrusion detection systems and firewalls mitigate attacks.
✅ Endpoint Security Testing → Examines vulnerabilities in employee devices, workstations, and internal software.
Traditional penetration testing follows established industry frameworks:
| Cyber Threat | Description | Penetration Testing Method |
|---|---|---|
| Phishing Attacks | Social engineering tactics used to steal credentials. | Social engineering penetration testing |
| Malware & Ransomware | Malicious programs designed to damage or encrypt data. | Endpoint security testing, malware analysis |
| Zero-Day Vulnerabilities | Exploiting unknown security flaws before patches are released. | Automated vulnerability scanning, ethical hacking |
| SQL Injection | Injecting malicious SQL code into a database. | Web application penetration testing (OWASP) |
| DDoS Attacks | Overwhelming networks with excessive traffic. | Stress testing, network penetration testing |
These methodologies provide structured, repeatable testing approaches, ensuring comprehensive vulnerability assessments in corporate environments.

Blockchain security encompasses decentralised security models designed to safeguard Web3 ecosystems, including decentralised finance (DeFi) platforms, non-fungible tokens (NFTs), decentralised autonomous organisations (DAOs), and cryptocurrency exchanges. Unlike centralised IT infrastructures, which rely on firewalls and endpoint security, blockchain security hinges on cryptographic integrity, decentralised governance, and secure consensus mechanisms.
Despite its tamper-resistant architecture, blockchain networks are not impervious to attacks. Cybercriminals exploit code vulnerabilities, governance weaknesses, and flawed cryptographic implementations to compromise blockchain-based systems.
Blockchain-based systems face a unique set of security threats, including:
Penetration testing in blockchain security differs significantly from traditional cybersecurity assessments. Instead of focusing on firewalls, endpoints, and access controls, blockchain penetration testing examines the security of smart contracts, decentralised governance mechanisms, and cryptographic implementations.
✅ Smart Contract Audits → Analyses Solidity code for vulnerabilities, such as reentrancy, integer overflows, and logic errors.
✅ Consensus Mechanism Testing → Evaluates resistance to 51% attacks and consensus failures.
✅ Cryptographic Assessment → Examines encryption models, private key management, and wallet security.
✅ Economic Attack Vectors → Identifies manipulation risks in DeFi lending protocols, oracle dependencies, and arbitrage opportunities.
For further details on blockchain security, refer to the OWASP Blockchain Security Framework (OWASP, 2024) and Ethereum Smart Contract Security Best Practices (Consensys, 2024).

The fundamental objectives of penetration testing remain the same—identifying vulnerabilities before threat actors exploit them. However, the techniques and focus areas vary between centralised and decentralised systems.
Traditional cybersecurity and blockchain security require distinct penetration testing tools, tailored to their respective environments.
| Aspect | Traditional Penetration Testing | Blockchain Penetration Testing |
|---|---|---|
| Security Model | Centralised systems with defined security perimeters. | Decentralised networks with distributed security mechanisms. |
| Primary Targets | Networks, servers, databases, web applications. | Smart contracts, consensus mechanisms, cryptographic protocols. |
| Testing Methodology | Network penetration testing, application security assessments. | Smart contract audits, cryptographic key security reviews. |
| Common Threats | Malware, phishing, zero-day vulnerabilities. | Reentrancy attacks, private key exposure, 51% attacks. |
| Penetration Testing Tools | Nmap, Metasploit, Burp Suite, Nessus. | Slither, Mythril, Echidna, Tenderly. |
To effectively secure both traditional and blockchain-based systems, penetration testers must apply best practices suited for each environment. Below are key strategies for both areas:
✅ Traditional Cybersecurity Penetration Testing Best Practices:
✅ Blockchain Security Penetration Testing Best Practices:
By following these tailored best practices, organizations can strengthen their security posture in both traditional and blockchain environments.
A leading Australian financial institution conducted a penetration test on its online banking infrastructure, uncovering critical API vulnerabilities that could have allowed attackers to bypass authentication mechanisms and extract sensitive customer data. The penetration test simulated real-world attack scenarios, including unauthorised API calls and injection attacks, revealing that several endpoints were insufficiently protected.
✔ API Security Hardening → The bank implemented rate limiting, stronger authentication mechanisms, and encryption for sensitive data transmissions.
✔ Enhanced Firewall & Access Control Policies → Security teams restricted API access based on least privilege principles.
✔ Regulatory Compliance Alignment → The penetration test helped the bank meet ACSC cybersecurity recommendations (ACSC, 2024).
A decentralised finance (DeFi) platform suffered a catastrophic loss of $100 million when attackers exploited a reentrancy vulnerability in its Ethereum-based smart contract. The penetration test was conducted post-attack, revealing that the contract lacked input validation and reentrancy guards, allowing hackers to drain liquidity through flash loans.
✔ Smart Contract Auditing Failure → The platform had not undergone a formal penetration test before deployment, leaving critical vulnerabilities unpatched.
✔ Lack of Reentrancy Protection → The smart contract failed to use the Checks-Effects-Interactions pattern, making it vulnerable to recursive function calls.
✔ Flash Loan Exploitation → Attackers manipulated token prices and drained liquidity pools within seconds.
For further insights into blockchain security exploits, refer to RugDoc’s repository of DeFi attack reports (RugDoc, 2024).
| Aspect | Traditional Cybersecurity (Bank API Test) | Blockchain Cybersecurity (DeFi Exploit) |
|---|---|---|
| Testing Focus | Network and API security, authentication bypass risks. | Smart contract vulnerabilities, reentrancy risks. |
| Vulnerability Identified | Exposed API endpoints allowing unauthorised data access. | Reentrancy bug allowing repeated fund withdrawals. |
| Security Patch | Implemented API rate limiting, encryption, and authentication improvements. | Deployed reentrancy guards and validated smart contract logic. |
| Financial Impact | No reported financial loss; security patch prevented future breaches. | $100M lost due to unaudited smart contract vulnerabilities. |
| Preventative Measures | Regular penetration testing, firewall updates, and compliance reviews. | Comprehensive smart contract audits, reentrancy protections, and security testing. |
The rapid expansion of decentralised finance (DeFi), decentralised autonomous organisations (DAOs), and cross-chain bridges is driving the evolution of blockchain security. As more assets and transactions shift to Web3 platforms, the sophistication of attack vectors is also increasing.
Without proactive penetration testing, smart contracts, governance mechanisms, and cryptographic implementations remain susceptible to exploitation.
To address emerging security threats, penetration testing in blockchain ecosystems is expected to adopt advanced methodologies, including:
For further insights, refer to the World Economic Forum’s Web3 Security Report (WEF, 2024).
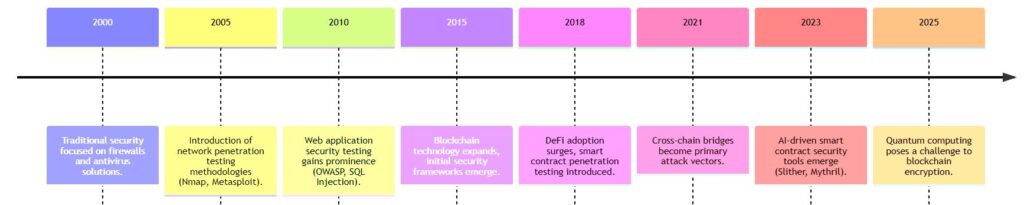
Cybersecurity threats continue to evolve, necessitating robust penetration testing methodologies across different environments.
To mitigate cybersecurity risks, organisations should adopt proactive security strategies:
✔ For Traditional IT: Regular network penetration testing, employee security training, and endpoint security audits.
✔ For Blockchain Projects: Smart contract audits, penetration testing, and rigorous cryptographic security assessments.
As Web3 technologies expand, penetration testing will play a crucial role in identifying vulnerabilities before they are exploited. Organisations must prioritise security testing to protect critical systems, digital assets, and sensitive data.
Cyber threats are becoming increasingly sophisticated, making penetration testing an essential defence strategy. Whether your organisation operates in finance, healthcare, or technology, ensuring network security and regulatory compliance is critical.
At Fort1, we provide comprehensive penetration testing services tailored to traditional IT environments. Strengthen your security posture, prevent breaches, and safeguard sensitive data with expert-led security assessments.
🔹 Learn more about Fort1’s cybersecurity solutions: Visit Fort1 🚀

Fort1 provides comprehensive cybersecurity solutions tailored to protect your business from evolving digital threats. With expertise in penetration testing, dark web monitoring, and managed detection services, we empower organisations to stay secure and resilient in the face of modern cyber challenges.
Copyright @2024 Fort1. All Rights Reserved by Fort1.