





Managed Vulnerability Assessment (MVA) is a proactive cybersecurity service designed to identify, evaluate, and remediate security vulnerabilities within an organisation’s IT infrastructure. By leveraging specialised tools and expert analysis, MVA ensures continuous monitoring and robust protection against evolving cyber threats.
The necessity of MVA cannot be overstated, particularly in the face of rising cybercrime. According to the Australian Cyber Security Centre (ACSC), over 76,000 cybercrime reports were filed in Australia in 2022, representing a 13% increase from the previous year. Many of these incidents exploited known vulnerabilities, underscoring the critical importance of identifying and addressing weaknesses before they can be exploited.
This article explores the key aspects of Managed Vulnerability Assessments, including how they work, the benefits they provide, and practical considerations for choosing a provider. Additionally, we will examine real-world examples of vulnerabilities that resulted in significant data breaches and discuss how MVA can serve as a foundational pillar of a comprehensive cybersecurity strategy.
Businesses face a myriad of threats and vulnerabilities that can undermine their cybersecurity posture, from outdated software and misconfigured systems to zero-day vulnerabilities exploited by malicious actors. According to a report by IBM, the average cost of a data breach in 2023 reached USD $4.45 million, with small to medium-sized businesses being disproportionately targeted. Many breaches occur due to unpatched vulnerabilities, highlighting the importance of timely identification and resolution.
Neglecting vulnerability assessments exposes organisations to significant risks, including financial losses, reputational damage, and regulatory penalties. For example, the 2017 Equifax breach, which compromised sensitive data of 147 million people, was traced back to an unpatched vulnerability in an open-source software library. Such incidents underscore how even a single vulnerability can result in catastrophic consequences.
Managed Vulnerability Assessments (MVA) enable businesses to stay ahead of these risks by systematically identifying and addressing vulnerabilities. Beyond mitigating immediate threats, these assessments support compliance with regulatory frameworks such as the Australian Privacy Act and the Essential Eight cybersecurity strategies.
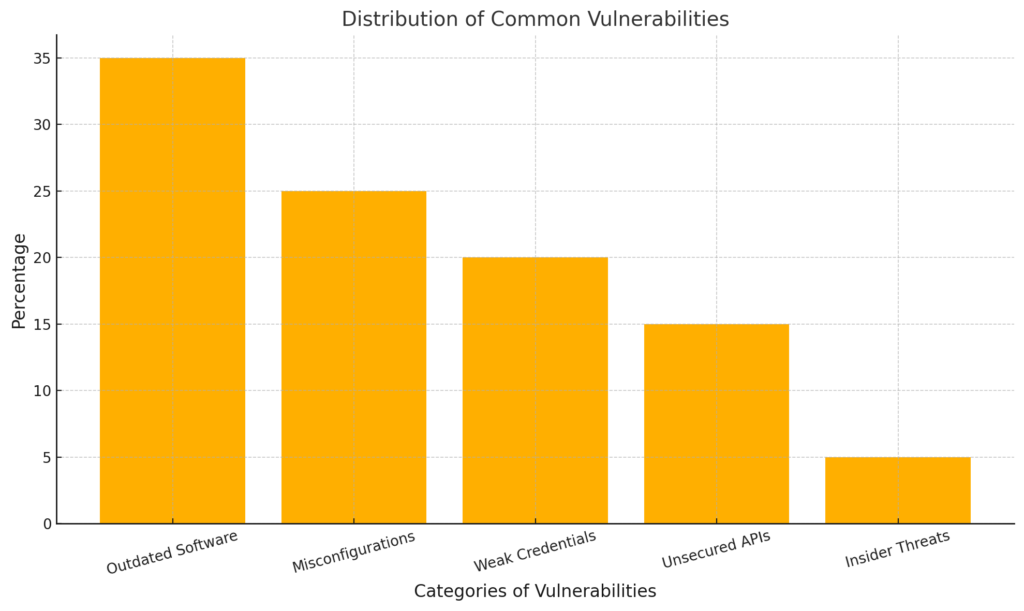
These insights emphasise that vulnerabilities are diverse but preventable with the right tools and expertise. A comprehensive approach to vulnerability assessment is not just a best practice—it is a critical defence strategy in an increasingly complex threat landscape.
Resource: Learn more from the IBM Cost of a Data Breach Report (https://www.ibm.com/security/data-breach).
Managed Vulnerability Assessments (MVA) follow a structured, multi-phase approach to systematically identify, evaluate, and address security vulnerabilities within an organisation’s IT environment. Each stage is designed to ensure comprehensive coverage and prioritisation of risks.
The process begins with an automated scan of the organisation’s assets, including servers, applications, endpoints, and cloud services. Advanced tools such as Nessus or Qualys are often employed to detect known vulnerabilities and misconfigurations. These tools leverage regularly updated vulnerability databases to ensure precision.
Once vulnerabilities are identified, they are categorised and prioritised based on their severity, potential impact, and exploitability. Critical issues that pose an immediate threat are flagged for urgent attention, while less critical issues are scheduled for remediation in future cycles.
Detailed reports are generated, providing actionable insights into vulnerabilities, affected systems, and remediation timelines. The reports also include compliance metrics to assist organisations in meeting standards such as ISO 27001 or the Essential Eight.
The final stage involves deploying patches, reconfiguring systems, or mitigating risks through other means. Follow-up scans are conducted to verify that vulnerabilities have been successfully addressed.
Automation is integral to this process, enabling continuous scanning and reducing manual effort. Tools like Rapid7 streamline complex tasks, allowing organisations to maintain a real-time view of their risk landscape.
By adhering to this structured approach, businesses can ensure a proactive stance against vulnerabilities, significantly reducing the likelihood of exploitation.
Managed Vulnerability Assessment (MVA) services provide a range of features that empower organisations to identify and address security risks effectively. These key features distinguish MVA as an essential tool for maintaining robust cybersecurity.
MVA services perform continuous or scheduled scans across an organisation’s IT infrastructure. This ensures vulnerabilities are detected promptly, enabling businesses to mitigate risks before they can be exploited.
Reports generated by MVA services go beyond identifying vulnerabilities; they provide detailed remediation steps tailored to each issue. These insights help technical teams prioritise their efforts, saving time and resources.
MVA services align with regulatory frameworks such as ISO 27001, the Essential Eight, and PCI DSS, helping organisations ensure compliance while improving their security posture.
Advanced MVA solutions integrate seamlessly with security platforms, such as SIEM tools, to deliver comprehensive threat intelligence and real-time monitoring.
These features collectively reduce the risk of breaches, support compliance with legal and industry standards, and enhance overall operational efficiency. For instance, businesses that implement regular vulnerability scans experience an average reduction of 50% in security incidents.
| Feature | Managed Vulnerability Assessment (MVA) | Traditional Vulnerability Assessment |
|---|---|---|
| Frequency | Regular or Continuous | Periodic |
| Reporting | Actionable with Remediation Steps | Basic Issue Identification |
| Compliance Support | Yes (aligned with standards) | Limited or None |
| Integration | Seamless with SIEM Tools | Standalone |
The combination of these features makes MVA an indispensable component of a proactive and resilient cybersecurity strategy.
Managed Vulnerability Assessments (MVAs) offer numerous benefits that significantly enhance an organisation’s cybersecurity, compliance, and operational efficiency. By systematically identifying and addressing vulnerabilities, MVAs empower businesses to minimise risks, streamline processes, and maintain regulatory adherence.
MVAs provide organisations with a proactive defence against cyber threats. For example, a retail company that regularly conducts vulnerability assessments identified a misconfigured payment system, which, if exploited, could have led to unauthorised access to customer data. Addressing the issue not only protected sensitive information but also prevented reputational damage and financial loss.
Regulatory frameworks, such as ISO 27001 and the Australian Privacy Act, mandate stringent security measures. MVAs facilitate compliance by providing detailed reports that align with these standards. Businesses can avoid hefty penalties by demonstrating their commitment to protecting customer data.
Automated and prioritised vulnerability assessments save significant time and resources. A hypothetical example is a medium-sized organisation that used an MVA service to scan its cloud infrastructure. Automation reduced the time spent on manual checks, allowing the IT team to focus on remediation and strategic projects.
These real-world scenarios underscore the tangible advantages of MVAs, making them an indispensable tool for organisations striving to maintain a robust and cost-effective cybersecurity posture.
Resource: For additional case studies on vulnerability assessments, visit Australian Cyber Security Centre.
Implementing vulnerability assessments presents several challenges that organisations must navigate to secure their IT infrastructure effectively. These challenges often stem from financial constraints, complexity, and resource allocation issues, particularly for small and medium-sized enterprises (SMEs).
The financial investment required for sophisticated tools and skilled personnel can be prohibitive for smaller organisations. However, this challenge can be mitigated by opting for managed vulnerability assessment (MVA) services, which offer scalable solutions without requiring extensive in-house expertise.
Modern IT environments often consist of diverse systems, applications, and networks, making comprehensive vulnerability assessments technically complex. Integrating automated tools such as Nessus or Qualys can streamline the process, reducing manual effort and increasing accuracy.
Organisations frequently struggle to allocate sufficient time and personnel for vulnerability management amidst competing priorities. This can be addressed by outsourcing to specialised MVA providers, allowing internal teams to focus on strategic initiatives while ensuring regular assessments are conducted.
By recognising and addressing these challenges, businesses can effectively implement vulnerability assessments and safeguard their assets against evolving cyber threats. With the right tools, strategies, and partnerships, even resource-constrained organisations can achieve a robust cybersecurity posture.
Selecting an effective Managed Vulnerability Assessment (MVA) provider is critical for achieving robust cybersecurity. Businesses should carefully evaluate providers based on their expertise, reporting capabilities, cost-effectiveness, and alignment with organisational needs.
A provider’s expertise in handling complex IT environments is paramount. Look for certifications such as ISO 27001 compliance and evidence of working with organisations of similar scale or industry. An experienced provider is better equipped to address industry-specific challenges and evolving cyber threats.
Detailed and actionable reports are essential for addressing vulnerabilities efficiently. Ensure the provider delivers reports that prioritise vulnerabilities, include remediation steps, and map findings to relevant compliance standards. Reporting should also support strategic decision-making by identifying long-term trends.
While price is a consideration, the cheapest option may not always deliver the required level of service. Evaluate the value offered, including access to advanced tools, 24/7 support, and automated features that enhance efficiency. Request transparent pricing structures to avoid unexpected costs.
Before finalising a provider, request a demo or trial service to evaluate their tools and reporting quality. Seek references or case studies from other clients to assess their reliability. Additionally, verify their ability to scale services as your organisation grows.
Choosing the right MVA provider requires balancing technical capabilities, business requirements, and budget considerations. With a strategic selection process, businesses can ensure their cybersecurity needs are met effectively.
Managed Vulnerability Assessments (MVA) are an indispensable component of a comprehensive cybersecurity strategy. By proactively identifying and mitigating vulnerabilities, organisations can safeguard their assets, ensure compliance with regulatory standards, and minimise the risk of costly breaches. As cyber threats continue to evolve, investing in MVA provides businesses with the confidence to navigate an increasingly complex digital environment.
To secure your organisation’s future, take the next step by exploring tailored MVA solutions. Partnering with a trusted provider such as Fort1 ensures access to expert guidance, cutting-edge tools, and actionable insights designed to protect your business.

Fort1 provides comprehensive cybersecurity solutions tailored to protect your business from evolving digital threats. With expertise in penetration testing, dark web monitoring, and managed detection services, we empower organisations to stay secure and resilient in the face of modern cyber challenges.
Copyright @2024 Fort1. All Rights Reserved by Fort1.